Table of Contents
Rudder 4.0 includes a policy mode setting, that allows two distinct behaviors:
- Audit: Test if the system is in the desired state, and report about it
- Enforce: Test if the system is in the desired state, if not, try to act to get to this state, and report about actions taken and final state
This allows for example to use Rudder as an audit tool or <<, _using_audit_mode_to_validate_a_policy_before_applying_it, to test a policy before enforcing it>>.
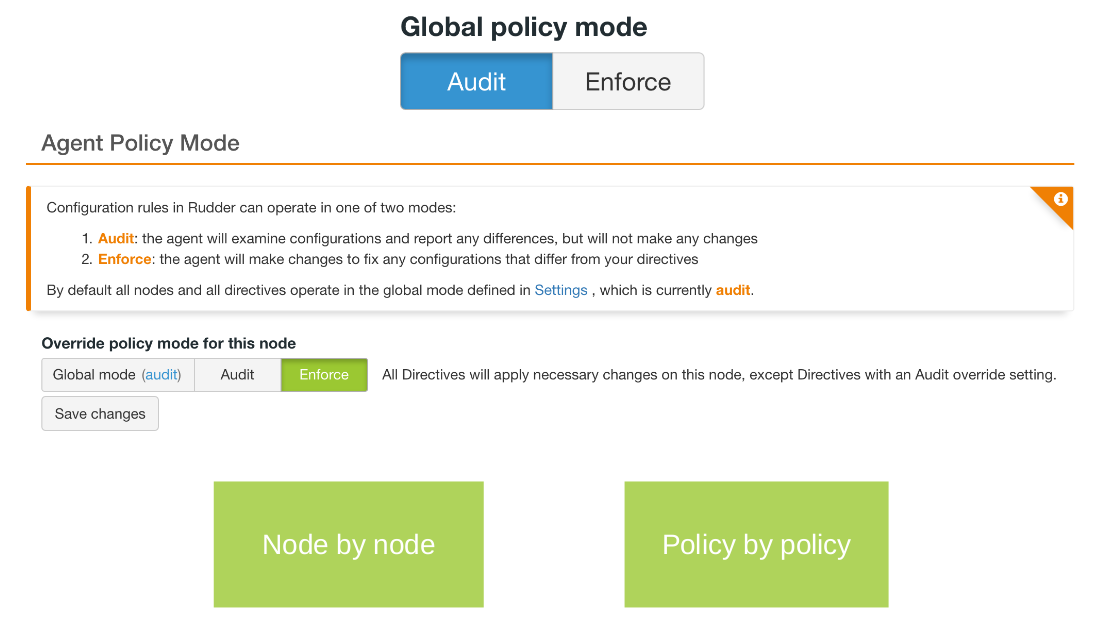
This mode can be set:
- Globally on the Rudder root server. In this can case there are two options: allow to override this mode on specific items, or use the global configuration everywhere.
- On a directive.
- On a node.
A lot of attention and several safeguards have been put in place to ensure that if you choose to use "Audit"
for a target, nothing will be changed on the node for that target (except Rudder's own configuration under /var/rudder), and only some harmless
commands will be run (like listing installed packages or refreshing package lists).
Nodes are fully aware of exactly what directives need to be executed in Audit or in Enforce mode, and the "rudder agent" command line has been enhanced to let you see the result with a glimpse: the first column in rudder agent run output is now the mode (A for Audit and E for Enforce), and the compliance summary is split by audit mode.
In addition to pre-existing technical reports, new ones have been added to report on "audit-compliant" (the check was OK), "audit-non-compliant" (the check was done, but the result is not the one expected), "audit-not-applicable" (the check is not applicable for that node, for example because of a limitation on the OS type), "audit-error" (the check wasn’t able to finish correctly) status.